PakAlumni Worldwide: The Global Social Network
The Global Social Network
Fireeye Founded by Pakistani-American Ashar Aziz Alerted US Government to Massive Cyber Hack
Massive cyberattack that recently targeted US government agencies and private companies, labeled the 'SolarWinds hack', was first discovered by US cybersecurity company FireEye, founded by a well-recognized Pakistani-American cybersecurity expert Ashar Aziz. Karachi-born Ashar served as the Chief Executive Officer (CEO) of Fireeye from 2004 to 2012. Ashar became the first Pakistani-American tech billionaire when the company stock soared after its initial public offering (IPO) in 2013. His net worth was last estimated at $268 million in 2015.
 |
| Ashar Aziz |
Solar Winds Hack:
Solarwinds is a cybersecurity toolset used by multiple US government agencies to detect and stop cyberattacks. It is alleged by American government agencies that some Russian-sponsored hackers managed to compromise Solarwinds software by adding malware to updates distributed by the company to its customers. It only came to light when the perpetrators attempted to break into the cybersecurity firm FireEye, which first disclosed a breach on December 9. Here's how Fireeye describes it:
"FireEye has uncovered a widespread campaign, that we are tracking as UNC2452. The actors behind this campaign gained access to numerous public and private organizations around the world. They gained access to victims via trojanized updates to SolarWind’s Orion IT monitoring and management software. This campaign may have begun as early as Spring 2020 and is currently ongoing. Post compromise activity following this supply chain compromise has included lateral movement and data theft. The campaign is the work of a highly skilled actor and the operation was conducted with significant operational security".
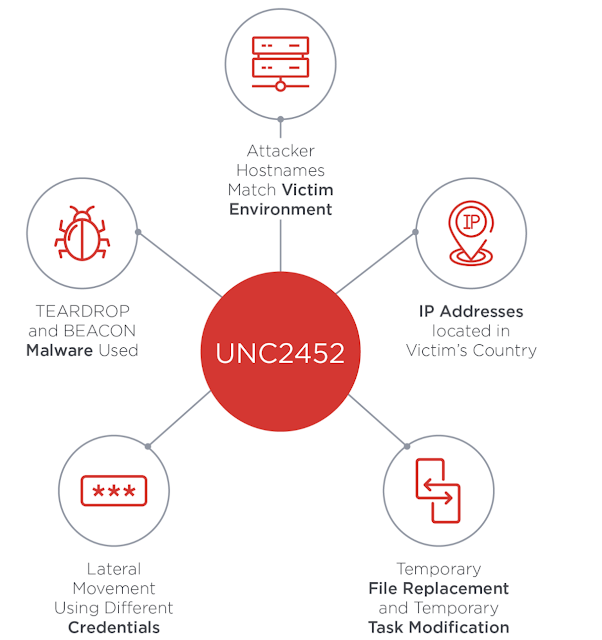 |
| Solarwinds Cyrber Hack. Source: Fireeye |
NED Alum Raises $100 Million For FinTech Startup in Silicon Valley
Pakistani-Americans Among Top 5 Most Upwardly Mobile Ethnic Groups
NED Alum Raghib Husain Sells Silicon Valley Company for $7.5 Billion
Pakistan's Tech Exports Surge Past $1 Billion in FY 2018
NED Alum Naveed Sherwani Raises $50 Million For SiFive Silicon Vall...
OPEN Silicon Valley Forum 2017: Pakistani Entrepreneurs Conference
Pakistani-American's Tech Unicorn Files For IPO at $1.6 Billion Val...
Pakistani-American Cofounders Sell Startup to Cisco for $610 million
Pakistani Brothers Spawned $20 Billion Security Software Industry
Pakistani-American Ashar Aziz's Fireeye Goes Public
Pakistani-American Pioneered 3D Technology in Orthodontics
Pakistani-Americans Enabling 2nd Machine Revolution
Pakistani-American Shahid Khan Richest South Asian in America
Two Pakistani-American Silicon Valley Techs Among Top 5 VC Deals
Pakistani-American's Game-Changing Vision
-
Comment by Riaz Haq on December 26, 2020 at 7:52pm
-
With Hacking, the United States Needs to Stop Playing the Victim The U.S. also uses cybertools to defend its interests. It’s the age of perpetual cyberconflict.
https://www.nytimes.com/2020/12/23/opinion/russia-united-states-hac...
By Paul R. Kolbe
The United States is, of course, engaged in the same type of operations at an even grander scale. We are active participants in an ambient cyberconflict that rages, largely unseen and unacknowledged, across the digital globe. This is a struggle that we can’t avoid, and there is no need to play the victim. Just as we use cybertools to defend our national interests, others will use cyberweapons against us.
The National Security Agency and Central Intelligence Agency exist to break into foreign information systems and steal secrets, and they are damn good at it. They, along with the Defense Department, regularly use cybertools to purloin intelligence from servers across the world and to place foreign information systems and industrial infrastructure at risk. Ones and zeros can be more effective weapons than bombs and missiles. The exposure of Stuxnet, the Snowden leaks and the theft of C.I.A. cybertools revealed the sophistication and extent of capabilities attributed to the United States.
The Pentagon’s cyberwar force, known as Cyber Command, overtly acknowledges, through its “defend forward” doctrine, that the government will target foreign entities and information systems to fight cyberattacks. In November 2018, Cyber Command reportedly disrupted the internet access of the computers of Russia’s Internet Research Agency, the organization responsible for the disinformation campaign during the 2016 U.S. midterm elections. In 2019, in response to Russian cyberincursions into the U.S. energy grid, Cyber Command reportedly placed malware tools on Russia systems that could enable the United States to turn out the lights in Moscow should a conflict between the two nations arise.
-
Comment by Riaz Haq on February 14, 2021 at 7:21pm
-
From CBS 60 Minutes:
https://www.cbsnews.com/news/solarwinds-hack-russia-cyberattack-60-...
Kevin Mandia (Fireye): Just like everybody working from home, we have two-factor authentication. A code pops up on our phone. We have to type in that code. And then we can log in. A FireEye employee was logging in, but the difference was our security staff looked at the login and we noticed that individual had two phones registered to their name. So our security employee called that person up and we asked, "Hey, did you actually register a second device on our network?" And our employee said, "No. It wasn't, it wasn't me."
Suspicious, FireEye turned its gaze inward, and saw intruders impersonating its employees snooping around inside their network, stealing FireEye's proprietary tools to test its clients defenses and intelligence reports on active cyber threats. The hackers left no evidence of how they broke in – no phishing expeditions, no malware.
Comment
Twitter Feed
Live Traffic Feed
Sponsored Links
South Asia Investor Review
Investor Information Blog
Haq's Musings
Riaz Haq's Current Affairs Blog
Please Bookmark This Page!
Blog Posts
IDEAS 2024: Pakistan Defense Industry's New Drones, Missiles and Loitering Munitions
The recently concluded IDEAS 2024, Pakistan's Biennial International Arms Expo in Karachi, featured the latest products offered by Pakistan's defense industry. These new products reflect new capabilities required by the Pakistani military for modern war-fighting to deter external enemies. The event hosted 550 exhibitors, including 340 international defense companies, as well as 350 civilian and military officials from 55 countries.
Pakistani defense manufacturers…
ContinuePosted by Riaz Haq on December 1, 2024 at 5:30pm
Barrick Gold CEO "Super-Excited" About Reko Diq Copper-Gold Mine Development in Pakistan
Barrick Gold CEO Mark Bristow says he’s “super excited” about the company’s Reko Diq copper-gold development in Pakistan. Speaking about the Pakistani mining project at a conference in the US State of Colorado, the South Africa-born Bristow said “This is like the early days in Chile, the Escondida discoveries and so on”, according to Mining.com, a leading industry publication. "It has enormous…
ContinuePosted by Riaz Haq on November 19, 2024 at 9:00am
© 2024 Created by Riaz Haq.
Powered by
![]()
You need to be a member of PakAlumni Worldwide: The Global Social Network to add comments!
Join PakAlumni Worldwide: The Global Social Network