PakAlumni Worldwide: The Global Social Network
The Global Social Network
America's High-Tech Warfare Against Pakistan?
The New York Times quotes unnamed US officials as acknowledging that the US "military planners suggested a far narrower computer-network attack to prevent Pakistani radars from spotting helicopters carrying Navy Seal commandos on the raid that killed Osama bin Laden on May 2." It says the idea of cyber attack on Pakistani air defense system was dropped, and radar-evading Black Hawk helicopters and stealthy RQ-170 Sentinel surveillance drone were instead used to for the raid in the Pakistani town of Abbottabad. The CIA spied on Osama bin Laden’s compound in Pakistan by video transmitted from a new bat-winged stealth drone, the RQ-170 Sentinel, which hovered high above Abbottabad for weeks before the raid. There are speculations that the US might be doing such aerial surveillance in other parts of Pakistan, particularly on Pakistan's nuclear installations.
Recently, officials at Creech Air Force Base in Nevada acknowledged a virus infecting the drone “cockpits” there, according to Wired magazine. The source of the virus has not been identified. Back in 2009, the Wall Street Journal reported that militants in Iraq used $26 off-the-shelf software to intercept live video feeds from U.S. Predator drones, potentially providing them with information they needed to evade or monitor U.S. military operations.
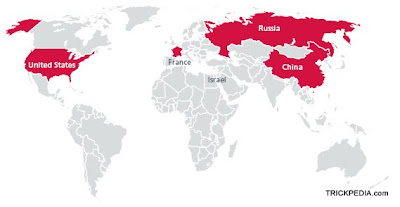
At the 2009 World Economic Forum, the U.S.-based security software firm McAfee's CEO Dave Walt reportedly told some attendees that China, the United States, Russia, Israel and France are among 20 countries locked in a cyberspace arms race and gearing up for possible Internet hostilities. He further said that the traditional defensive stance of government computer infrastructures has shifted in recent years to a more offensive posture aimed at espionage, and deliberate disruption of critical networks in both government and private sectors. Such attacks could disrupt not only command and control for modern weapon systems such as ballistic missiles, but also critical civilian systems including banking, electrical grid, telecommunications, transportation, etc, and bring life to a screeching halt.
In a Sept 2010 report, the Wall Street Journal quoted cyber security specialists saying that "many countries including the U.S., Russia, China, Israel, the U.K., Pakistan, India and North and South Korea have developed sophisticated cyber weapons that can repeatedly penetrate and have the ability to destroy computer networks".
Last year, Chinese hackers apparently succeeded in downloading source code and bugs databases from Google, Adobe and dozens of other high-profile companies using unprecedented tactics that combined encryption, stealth programming and an unknown hole in Internet Explorer, according to new details released by the anti-virus firm McAfee and reported by Wired magazine. These hack attacks were disguised by the use of sophisticated encryption, and targeted at least 34 companies in the technology, financial and defense sectors, exploiting a vulnerability in Adobe’s Reader and Acrobat applications.
While the Chinese cyber attacks on US and India often get wide and deep coverage in the western media, a lower profile, small-scale cyber warfare is also raging in the shadows between India and Pakistan, according to some reports. These reports indicate that around 40-50 Indian sites are being attacked by Pakistani hackers on a daily basis whereas around 10 Pakistani sites are being hit by their Indian counterparts.
Here is how Robert X. Cringeley described the potential effects of full-scale India-Pakistan cyber war in a June 2009 blog post captioned "Collateral Damage":
"Forget for the moment about data incursions within the DC beltway, what happens when Pakistan takes down the Internet in India? Here we have technologically sophisticated regional rivals who have gone to war periodically for six decades. There will be more wars between these two. And to think that Pakistan or India are incapable or unlikely to take such action against the Internet is simply naive. The next time these two nations fight YOU KNOW there will be a cyber component to that war.
And with what effect on the U.S.? It will go far beyond nuking customer support for nearly every bank and PC company, though that’s sure to happen. A strategic component of any such attack would be to hobble tech services in both economies by destroying source code repositories. And an interesting aspect of destroying such repositories — in Third World countries OR in the U.S. — is that the logical bet is to destroy them all without regard to what they contain, which for the most part negates any effort to obscure those contents."
Coming back to the US, it is no secret that the Pentagon and the CIA have increasingly been using America's significant technology edge for war fighting in many parts of the world in recent years. One example is the growing fleet of the remotely controlled stealthy drones being deployed in Afghanistan, Pakistan, Iraq, Yemen and elsewhere for espionage and attacks. Among other new developments, the modern drone is just one of the ways to fight wars covertly in remote places at low cost to America in terms of dollars and casualties, often without so munch as declaring such wars.
The Pentagon now has some 7,000 UAVs, compared with fewer 50 just 10 years ago. The US Air Force is now anticipating a decrease in manned aircraft but expects its number of “multirole” aerial drones like the Reaper — the ones that spy as well as strike — to nearly quadruple, to 536, according to NY Times. Already the Air Force is training more remote pilots, 350 this year alone, than all of the fighter and bomber pilots combined.
The covert nature of drone warfare is particularly true outside Afghanistan and Iraq which are declared wars. In Pakistan, for instance, the secret war is being fought by the CIA, an intelligence agency, not the American military. This war is not even publicly acknowledged by the US administration, and it's a clear violation of international laws and all conventions of war.
The US politicians, spies and generals seem to be calculating that the American people would be more willing to support such wars if they don't bust the US budget and result in as few American body bags as possible. However, this calculation ignores the basic fact that most international conflicts, including terrorism, are essentially political in nature, and must be solved by political rather than the military means.
Related Links:
Haq's Musings
Cyber Attacks in India, Pakistan and China
Nature of Future India-Pakistan Warfare
ITU Internet Access Data by Countries
Foreign Origin of India's Agni Missiles
Pakistan's Space Capabilities
Seeing Bin Laden's Death in Wider Perspective
Pakistan's Multi-Billion Dollar IT Industry
John Arquilla: Go on the Cyberoffensive
Pakistan Defense Industry Going High Tech
India-Pakistan Military Balance
21st Century High Tech Warfare
-
Comment by Riaz Haq on July 18, 2016 at 10:21pm
-
Would #Turkey be justified in kidnapping or drone-killing #Gulen in #Pennsylvania? #TurkeyCoupAttempt http://interc.pt/29I2fC8 by @ggreenwald
TURKEY’S PRESIDENT RECEP Tayyip Erdogan places the blame for this weekend’s failed coup attempt on an Islamic preacher and one-time ally, Fethullah Gulen (above), who now resides in Pennsylvania with a green card. Erdogan is demanding the U.S. extradite Gulen, citing prior extraditions by the Turkish government of terror suspects demanded by the U.S.: “Now we’re saying deliver this guy who’s on our terrorist list to us.” Erdogan has been requesting Gulen’s extradition from the U.S. for at least two years, on the ground that he has been subverting the Turkish government while harbored by the U.S. Thus far, the U.S. is refusing, with Secretary of State John Kerry demanding of Turkey: “Give us the evidence, show us the evidence. We need a solid legal foundation that meets the standard of extradition.”
In light of the presence on U.S. soil of someone the Turkish government regards as a “terrorist” and a direct threat to its national security, would Turkey be justified in dispatching a weaponized drone over Pennsylvania to find and kill Gulen if the U.S. continues to refuse to turn him over, or sending covert operatives to kidnap him? That was the question posed yesterday by Col. Morris Davis, former chief prosecutor of Guantánamo’s military commissions who resigned in protest over the use of torture-obtained evidence:
That question, of course, is raised by the fact that the U.S. has spent many years now doing exactly this: employing various means — including but not limited to drones — to abduct and kill people in multiple countries whom it has unilaterally decided (with no legal process) are “terrorists” or who otherwise are alleged to pose a threat to its national security. Since it cannot possibly be the case that the U.S. possesses legal rights that no other country can claim — right? — the question naturally arises whether Turkey would be entitled to abduct or kill someone it regards as a terrorist when the U.S. is harboring him and refuses to turn him over.
The only viable objection to Turkey’s assertion of this authority would be to claim that the U.S. limits its operations to places where lawlessness prevails, something that is not true of Pennsylvania. But this is an inaccurate description of the U.S.’s asserted entitlement. In fact, after 9/11, the U.S. threatened Afghanistan with bombing and invasion unless the Taliban government immediately turned over Osama bin Laden, and the Taliban’s answer was strikingly similar to what the U.S. just told Turkey about Gulen:
-
Comment by Riaz Haq on August 21, 2016 at 5:25pm
-
#US #NSA used #malware to spy on #Pakistani civilian, military leadership. #Pakistan #NSAhack #Snowden
http://www.dawn.com/news/1279013/nsa-used-malware-to-spy-on-pakista...
The United States' clandestine National Security Agency (NSA) allegedly spied on top civil-military leadership in Pakistan using malware, The Intercept reported.
Malware SECONDDATE allegedly built by the NSA was used by agency hackers to breach "targets in Pakistan’s National Telecommunications Corporation’s (NTC) VIP Division", which contained documents pertaining to "the backbone of Pakistan’s Green Line communications network" used by "civilian and military leadership", according to an April 2013 presentation document obtained by The Intercept.
The file appears to be a 'top secret' presentation originating from the NSA's SigDev division.
SECONDDATE is described as a tool that intercepts web requests and redirects browsers on target computers to an NSA web server. The server then infects the web requests with malware.
The malware server, also known as FOXACID, has been described in earlier leaks made by former NSA contractor Edward Snowden.
SECONDDATE, however, is just one method the NSA allegedly uses to redirect a target's browser to the FOXACID server. Others involve exploiting bugs in commonly used email providers by sending spam or malicious links that lead to the server, The Intercept said.
Another document obtained by The Intercept, an NSA Special Source Operations division newsletter describes how agency software other than SECONDDATE was used to repeatedly direct targets in Pakistan to the FOXACID servers to infect target computers.
The Intercept confirmed the "authenticity" of the SECONDDATE malware by means of a data leak reportedly made by Snowden.
Snowden released a classified top-secret agency draft manual for implanting malware which instructs NSA operators to track their use of a malware programme through a 16-character string ─ the same string which appears in the SECONDDATE code leaked by a group called ShadowBrokers.
ShadowBrokers last week announced that SECONDDATE was part of a group of NSA-built 'cyber weapons' that it was auctioning off.
Although it is unclear how the code for the software leaked and was obtained by ShadowBrokers, The Intercept claims "the malware is covered with NSA's virtual fingerprints and clearly originates from the agency".
The ShadowBrokers auction of SECONDDATE is the first time any full copies of NSA software have been made available to the public.
"The person or persons who stole this information might have used them against us," Johns Hopkins University cryptographer Matthew Green said on the dangers of such software becoming available to the public.
Speaking to The Intercept, Green said that such exploits could be used to target anyone using a vulnerable router. "This is the equivalent of leaving lockpicking tools lying around a high school cafeteria. It’s worse, in fact, because many of these exploits are not available through any other means, so they’re just now coming to the attention of the firewall and router manufacturers that need to fix them, as well as the customers that are vulnerable."
The Intercept has in the past published a number of reports from documents released by Snowden. The site’s editors include Glenn Greenwald, who won a Pulitzer Prize for his work in reporting on the whistleblower’s revelations.
https://theintercept.com/2016/08/19/the-nsa-was-hacked-snowden-docu...
Comment
- ‹ Previous
- 1
- 2
- Next ›
Twitter Feed
Live Traffic Feed
Sponsored Links
South Asia Investor Review
Investor Information Blog
Haq's Musings
Riaz Haq's Current Affairs Blog
Please Bookmark This Page!
Blog Posts
Major Hindu American Group Distances Itself From Modi's India
"We are not proxies for India in the US", wrote Suhag Shukla, co-founder and executive director of the Hindu American Foundation (HAF) in a recent article for The Print, an Indian media outlet. This was written in response to Indian diplomat-politician Shashi Tharoor's criticism that the Indian-American diaspora was largely silent on the Trump administration policies hurting India. …
ContinuePosted by Riaz Haq on October 11, 2025 at 2:00pm
Gaza Genocide: Is the Powerful Israel Lobby AIPAC Losing Influence?
Several Congressional Democrats have recently refused campaign contributions from AIPAC, the powerful Israel lobby, according to media reports. “Democrats who once counted AIPAC among their top donors have in recent weeks refused to take the group’s donations”, says a New York Times story titled "Democrats Pull Away From AIPAC, Reflecting a Broader Shift". “AIPAC is…
ContinuePosted by Riaz Haq on October 5, 2025 at 4:00pm — 7 Comments
© 2025 Created by Riaz Haq.
Powered by
![]()
You need to be a member of PakAlumni Worldwide: The Global Social Network to add comments!
Join PakAlumni Worldwide: The Global Social Network